Static Code Analysis: Everything You Need to Know

In a recent survey report, Incredibuild asked 300 senior IT managers about the technologies and methodologies that they most used to accelerate and improve the development cycle.
More than three-quarters (76%) said they use static code analysis, and another 11% said they planned to implement it in the coming year. But not everyone has embraced automation just yet.
Software development teams are always looking for ways to increase both the speed of development processes and the reliability of their software. According to our 2024 State of Software Quality report, 58% of developers say not having enough time is the most common challenge during code reviews. The best way to achieve speed and reliability is to identify and fix code issues as early in the development process.
Static code analysis (SCA) can help you do just that.
We chatted with several experts to find out what SCA can do, how to use it without slowing down development, and their real-life experience with these practices.
What Is Static Code Analysis?
Static code analysis is a popular software development practice performed in the early “creation” stages of development. In this analysis process, developers examine the source code they’ve created before executing it.
Static code analysis is used to identify potential vulnerabilities, errors, and deviations from coding standards early in the development process. It also helps teams comply with coding guidelines like MISRA and industry standards like ISO 26262.
Ritesh Joshi, CTO, Let Set Go recommends thinking of SCA as a spell and grammar check for your code that automatically scans for bugs and vulnerabilities.
“Tools like SonarQube and Codacy are great examples. Integrating SCA without slowing development is key. Treat it like regular checkups, not major surgery. Run SCA frequently on small code chunks—ideally with every commit. This "shift-left" approach catches issues early, when they're cheaper to fix.”
While static code analysis helps maintain quality, don’t throw it into a workflow without a plan.
“Enforcing checks at the pull request level allows developers to catch issues before code merges. A single overlooked bug can take 10-15 hours to debug later, while fixing it during development takes less than 30 minutes.”- Thomas Franklin, CEO, Swapped.
When implemented effectively, static code analysis and the early error detection it offers can help your development team achieve the following:
- Code consistency through enforcing coding standards and best practices that keep your codebase maintainable and readable.
- Stronger code security through catching potential vulnerabilities like SQL injection, buffer overflows, and XSS attacks.
- Cost savings by detecting and fixing issues early in development instead of addressing them in later stages or post-release, when fixes become more complex and issues may have already affected customers.

So, what’s the difference between code analysis and code review? In a typical code review process, developers manually read their code line-by-line to review it for potential issues. Code analysis uses automated tools to analyze your code against pre-written checks that identify issues for you.
Development teams also perform static code analysis to create an automated feedback loop within their team that helps catch code issues early. The earlier you identify coding errors, the easier and faster it will be to resolve them.
Automated tools that teams use to perform this type of code analysis are called static code analyzers or simply static code analysis tools. An example of a popular static code analyzer is a linter. This automated tool focuses on code style and formatting by checking your code against predefined rules, conventions, and best practices.
Code quality tools can integrate into text editors and integrated development environments (IDEs) to give developers real-time feedback and error detection as they write their code.
Static Analysis vs. Dynamic Analysis
Static and dynamic code analysis are processes that help you detect defects in your code. The difference lies in the stage of the development cycle in which the analysis is performed.
Static analysis identifies issues before you run the program. The process occurs in a non-run-time environment between the time you create the code and perform unit testing.
Dynamic analysis identifies issues after you run the program (during unit testing).
In this process, you test code while executing on a real or virtual processor. Dynamic analysis is especially effective for finding subtle defects and vulnerabilities because it looks at the code’s interaction with other databases, servers, and services.
However, dynamic analysis comes with some important caveats. For example, it will only find faults in the specific excerpt of the executed code, not the entire codebase.
Both are essential processes. Static analysis ensures fewer defects during unit testing, and dynamic analysis catches issues your static analysis tools might have missed. To achieve the highest possible level of test coverage, combine the two methods.
How Static Code Analysis Works
The first step in the static code analysis process is source code input. Developers make their source code files or a specific codebase available to the static analysis tool they’re using.
A compiler then scans the source code. A compiler is a program that translates your source code from human-readable to machine code that’s computer-executable. The compiler breaks your code down into smaller pieces, known as tokens. If your source code is a book or short story, tokens are the words used to create it.
The next stage of the process is parsing. Parsers take the tokens, confirm that the tokens are sequenced in a way that makes sense according to the programming language you are using, and organize them into a structure called an abstract syntax tree (AST), which is an abstract representation of the code’s structure.
Now, your static analysis tool can start checking your code. Depending on which one you’re using, the tool performs analysis techniques, including:
- Syntax analysis that checks for syntax errors and coding style violations to ensure code consistency and readability.
- Data flow analysis that traces the flow of data within the code to find issues related to variable usage, uninitialized variables, and data dependencies to detect potential runtime errors.
- Control flow analysis that examines the program’s control flow paths to identify issues like dead code, unreachable code, and infinite loops to enhance code reliability and performance.
- Security vulnerability analysis that identifies vulnerabilities such as SQL injection, Cross-Site Scripting (XSS), and buffer overflows.
Suppose the tool identifies potential issues, like violations of coding standards or security vulnerabilities. In that case, the static code analyzer generates a report listing all the issues found and often provides other details, such as the suspected severity of the issue. Some static code analysis tools even offer suggested fixes for the found issues.
Benefits of Static Code Analysis
Static code analysis is one of the pillars of the “shift left testing movement,” which prioritizes pushing software testing into the earliest possible stages of development. When you’re performing source code analysis early and frequently, you can find and fix problems before they reach the product and they become more complicated and expensive to fix.
Early source code testing via static analysis helps your team achieve the following:
- Consistency by enforcing coding standards, patterns, and best practices.
- Enhanced security by finding security flaws early to decrease the risk of data breaches occurring.
- Improved efficiency by automating testing instead of having to perform manual code reviews.
- Better maintainability by fixing issues quickly and making your codebase less error-prone over time as it grows.
When you can create and ship code faster while maintaining consistency, quality, security, and maintainability, you can cut your development costs—and even increase revenue—which is the main benefit of having an efficient and effective static code analysis process.
According to a recent Consortium for Information and Software Quality report, software quality issues cost companies more than $2.08 trillion annually. The study also found that in a 25-year application lifecycle, companies spend nearly half of their money on identifying and fixing errors, making bug detection and correction a software company’s single greatest expense.
Static code analysis also helps companies avoid another huge expense—dealing with security breaches and their impact. The global average cost of a data breach in 2023 was $4.45 million, according to IBM’s most recent Cost of a Data Breach Report, an increase of 15% since 2020.
Static code analysis can also increase your team’s productivity, reducing the time and cost of development. Undo’s recent research report found that 26% of developer time is spent reproducing and fixing failing tests, adding that the total estimated value of salary spent on this work costs businesses $61 billion annually.
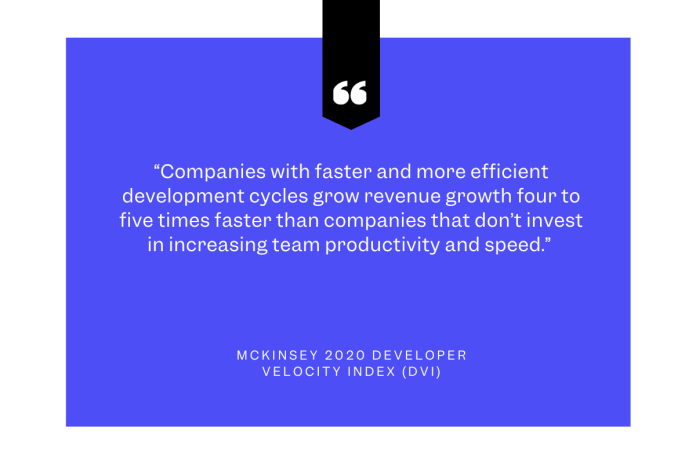
McKinsey’s 2020 report on developer velocity found that companies with faster and more efficient development cycles grow revenue four to five times faster than companies that don’t invest in increasing team productivity and speed.
Incredibuild’s 2022 survey report found that 21% of software leaders want access to better debugging tools to improve their day-to-day work and save development time.

Potential Limitations of Static Code Analysis
When you can catch and fix code issues early, you’re already on a great path toward improving code quality and the velocity of your development cycle. However, static code analysis is not a fool-proof solution that guarantees perfect code.
Static analysis cannot catch every issue all the time. Static analyzers typically don’t detect issues related to runtime behavior and external dependencies. They also may not understand domain-specific logic. Static code analyzers are also prone to producing false positives.
Here are some of the common limitations of using static code analysis.
False Positives and Negatives
Static code analysis tools can sometimes flag code as problematic when it is actually safe (false positives). Conversely, they may miss real issues (false negatives), leading to overlooked vulnerabilities.
To ensure the accuracy of the findings, developers need to manually review and verify the flagged issues, which can be time-consuming and may lead to fatigue.
Artem Razin, CEO, Softanics shared how their team dealt with false positives:
“Many tools generate thousands of warnings, especially for older codebases, making it difficult to extract meaningful insights. To address this, we tested multiple tools and prioritized those with the lowest false positive rates. The key is to invest time in configuring the tool to suit your project's needs—this setup phase is crucial for long-term success. Once properly tuned, the tool becomes a valuable asset rather than a burden.”
Limited Runtime Analysis
Because static analysis doesn’t execute the code, it might not detect runtime issues such as memory leaks, race conditions, or errors that occur based on a user’s specific inputs. These types of problems often emerge only during actual application execution, which makes them outside the scope of what static analysis can identify.
Combining static analysis with dynamic testing methods is essential for a more comprehensive view of potential issues.
Complex Code Challenges
Some static analysis tools can struggle to accurately identify problems in code with intricate business logic, complex data flows, or highly dynamic behavior. The tool may misinterpret complex patterns or fail to recognize context-specific risks, especially when the code deviates from standard or simple structures.
In these cases, human intervention is needed to ensure that complex scenarios are correctly assessed.
Language Specificity
Different programming languages have different syntaxes and semantics, which means static analysis tools need tailored rules for each language. A tool that works well for one language may not perform as effectively for another.
Organizations must ensure they choose or configure tools that work well with the languages they use.
External Dependencies
Static analysis tools often cannot fully evaluate the risks posed by external libraries, frameworks, or APIs that the code relies on. These third-party dependencies can introduce vulnerabilities that static analysis cannot detect, leaving potential security gaps in the codebase.
To address this, organizations should use additional tools like Software Composition Analysis (SCA) and regularly audit third-party packages to ensure they are secure.
Configuration Complexity
Configuring static analysis tools can be challenging, especially when balancing sensitivity settings. If the tool is set too aggressively, it may produce excessive false positives, flagging harmless code as risky.
Conversely, if the settings are too lenient, it may miss important vulnerabilities. Fine-tuning the configuration to strike the right balance requires expertise and ongoing maintenance.
Manual Interpretation Needed
Even with automated static analysis, the results often require manual interpretation by developers. Identifying whether a flagged issue is truly a vulnerability or just a coding style choice can be subjective.
Developers must assess the severity of each finding and determine whether it poses a real risk to security or functionality, which can add an extra layer of complexity to the process.
Potential for False Sense of Security
Relying solely on static analysis tools without integrating other testing methods can lead to a false sense of security. Since static analysis may miss runtime issues or complex vulnerabilities, using it as the only source of validation can create gaps in coverage.
It’s important to use a multi-faceted testing approach — incorporating both static and dynamic analysis — to get a more complete picture of the code’s security and quality.
What to Look for in a Static Code Analysis Tool
“Writing code without static analysis is like sailing without a compass: sooner or later you will end up off course.”- Eduard Andrei Capanu, Technical Leader (FE) - MVP Microsoft, Rebrandly.
When evaluating static code analysis tools, it’s important to select one that offers the features needed in your project or business. Consider the following key factors to ensure you make the right choice.
Language Support
When selecting a static code analysis tool, ensure it supports your team's programming languages. Whether you work with common languages like Java, Python, and JavaScript or more specialized ones like Rust or Go, the tool should be versatile enough to handle all relevant languages in your tech stack.
If your project uses multiple technologies, look for a solution that supports a wide range of languages so you can ensure consistent code quality across your entire application.
Accuracy and Effectiveness
The core function of a static code analysis tool is to detect code issues. You want a tool with high accuracy—low false positives (incorrectly marking non-issues as problems) and low false negatives (missing actual issues).
In addition, the tool should effectively identify critical security vulnerabilities, such as SQL injections and cross-site scripting (XSS), as well as code smells, anti-patterns, and performance bottlenecks. This enables developers to prioritize issues that could have the most significant impact on both security and application performance.
Integration With Development Workflows
A static code analysis tool should seamlessly integrate into your existing development processes. This includes compatibility with popular Integrated Development Environments (IDEs) like VS Code or IntelliJ and your CI/CD pipelines that automate builds and tests.
Before settling on a tool, confirm that it integrates with version control systems such as Git, GitHub, GitLab, or Bitbucket to ensure that code quality checks are performed automatically as part of your development lifecycle. This ensures consistent quality assurance without disrupting the flow of your team.
Security Rule Coverage
Security is a top concern for most development teams, and a good static code analysis tool should include robust rule sets for identifying security vulnerabilities.
Check whether the tool covers industry standards like the OWASP Top 10 (common web application vulnerabilities), the Common Weakness Enumeration (CWE), and the SANS 25 (critical software vulnerabilities).
The tool should also catch issues like insecure dependencies, injection attacks, misconfigurations, and data exposure problems to help safeguard your application from potential security risks.
Customizability
Every project has unique requirements, and so do development teams. A flexible static code analysis tool allows you to define custom rules and policies based on the specific needs of your project or organization.
Customizability can include adjusting severity levels for issues, defining acceptable coding practices, or aligning with compliance guidelines. It should also support team-specific coding standards to ensure that the tool fits into your workflow rather than imposing one-size-fits-all checks.
Scalability and Performance
Static code analysis can become resource-intensive, especially when dealing with large codebases. Before committing to a tool, check the time it takes to run a full scan on small and large codebases. Ideally, the right tool should perform fast, accurate analysis without slowing down your development or build process.
Mukul Juneja, Director & CTO, Muoro shared a real-life example of how they handled this:
“Our team was working on a fintech application that needed airtight security. Everything was moving fast: new features, integrations, and client requests. But security vulnerabilities kept creeping in. Manually reviewing code wasn't scalable, and last-minute security fixes were slowing down releases. That's when we turned to static code analysis. But implementing it without slowing down development? That took smart rule management and the right tools. Here's how we made it work:
-
Automated scans in CI/CD - Security checks ran on pull requests, preventing risky code from merging.
-
Used rule-based detection - Predefined security rules flagged vulnerabilities without unnecessary noise.
-
Leveraged remediation guidance - Tools suggested fixes, so developers could resolve issues faster.
-
Ran incremental scans - Instead of scanning the whole codebase, we analyzed only the changes.
-
Integrated with IDEs - Developers got real-time feedback, reducing back-and-forth fixes.”
If your project is expected to scale, ensure the tool can handle increasing complexity and code size over time. Cloud-based solutions offer flexibility and scalability, while on-premise options may better suit teams with stricter security and performance requirements.
Actionable Reporting and Insights
The value of static code analysis lies not just in finding issues, but in providing actionable insights that drive improvement. A good tool will provide clear, detailed reports that categorize issues by severity, making it easy for developers to prioritize what to fix first.
In addition to reports, dashboards and metrics help track code quality trends over time, giving the team a clear picture of progress and potential areas for improvement in the codebase.
Developer-friendliness
For static code analysis to be effective, it needs to be easy for developers to use and interpret. The tool should offer an intuitive user interface (UI) or command-line interface (CLI) with clear explanations for each identified issue.
Additionally, it should suggest practical fixes for problems to help developers resolve them efficiently. A developer-friendly tool promotes adoption and encourages continuous code quality improvement without overwhelming the team with complexity.
“Too much noise kills adoption. A tool that throws hundreds of alerts per scan ends up ignored. Tuning rule sets to fit project needs prevents unnecessary disruptions. If a specific pattern consistently triggers false positives, adding exceptions keeps scans relevant. The goal is catching meaningful problems, not overwhelming developers with pointless warnings. Reducing false positives by 50% can cut review time from hours to minutes.” - Thomas Franklin, CEO, Swapped.
Support for Compliance and Governance
Many industries require adherence to specific regulatory standards. A static code analysis tool should be able to support compliance with regulations such as GDPR, HIPAA, and ISO 27001.
It should provide features like audit logs and detailed compliance reports, which are essential for tracking the state of code quality in highly regulated environments. This ensures that your development process meets legal and security requirements while minimizing risk.
Cost and Licensing
Static code analysis tools come in both open-source and commercial forms. While open-source tools may be free, they often require more manual configuration or lack support for advanced features. Commercial tools typically come with a price tag but offer additional functionalities like enterprise support, more comprehensive rule sets, and better integration.
Evaluate the tool’s pricing model carefully to ensure it fits within your team's budget and scales as your project grows. Transparent pricing helps avoid unexpected costs down the line.
Types of Static Analysis
Organizations can leverage different types of static analysis to improve code quality, security, and maintainability. These methods focus on different aspects of the code, ensuring a comprehensive approach to static code analysis.
| Type of Static Analysis | Description | Key Benefits |
|---|---|---|
| Control Flow Analysis | Examines the sequence of program execution to detect unreachable code, infinite loops, and logic issues. | Improves code efficiency, eliminates dead code, and ensures logical soundness. |
| Data Flow Analysis | Tracks variable initialization, usage, and potential leaks throughout the program. | Prevents uninitialized variables, reduces memory waste, and enhances data security. |
| Fault/Failure Analysis | Identifies weak points that could cause system crashes or unexpected failures. | Enhances software reliability and resilience under different scenarios and loads. |
| Interface Analysis | Evaluates how modules and components interact, checking for API misuses and parameter mismatches. | Ensures smooth integration between components and reduces communication-related bugs. |
| Formal Analysis | Uses mathematical models to rigorously verify code correctness under all conditions. | Essential for safety-critical systems, ensuring code behaves as expected in every possible scenario. |
| Style and Cosmetic Analysis | Enforces coding standards, checking for formatting, indentation, and naming conventions. | Promotes code readability, consistency, and easier collaboration among team members. |
| Design Properties Analysis | Assesses architectural complexity, module dependencies, and maintainability. | Helps simplify code, reduce unnecessary dependencies, and improve long-term code maintainability. |
| Error Checking | Identifies syntax errors, undefined behaviors, and best practice violations. | Acts as a first line of defense against simple, potentially harmful bugs. |
| Predictive Analysis | Estimates runtime behavior based on code patterns, detecting performance and concurrency issues. | Helps teams optimize code for performance and scalability before deployment. |
Control Flow Analysis
Control flow analysis examines how different parts of a program execute and tracks the sequence in which statements and functions are called. It helps identify unreachable code, infinite loops, and dead ends in the logic that could result in inefficient execution or errors.
Incorporating control flow analysis is a great way to make the code more efficient and simple. It also ensures that all parts of the code are functional and logically sound.
Data Flow Analysis
Software teams use data flow analysis to ensure that variables and data structures are properly initialized, assigned, and used throughout the program. This type of analysis looks for issues like uninitialized variables, improper memory allocations, and data leaks.
When we trace how data moves and transforms within the program, it’s easier to identify bugs that might lead to unpredictable behavior, memory waste, or security vulnerabilities related to sensitive data handling.
Fault/Failure Analysis
Fault or failure analysis allows teams to uncover potential faults or weak points in software components that could lead to system failures, crashes, or vulnerabilities. It detects scenarios where the software might behave incorrectly, such as during high-load situations or when interacting with unexpected inputs.
This type of analysis is essential for identifying bugs that could compromise software reliability and security, ensuring a more stable product.
Interface Analysis
APIs play a critical role in modern software development as they enable seamless communication between software systems. Interface analysis evaluates how different modules or components of a program interact with each other, ensuring proper communication and data exchange.
It looks for issues in function calls, API usage, and mismatched parameters that could cause errors or integration failures. This ensures that each part of the system works seamlessly with others, maintaining the integrity of the overall software architecture.
Formal Analysis
Formal analysis uses mathematical models and techniques to rigorously verify whether the code behaves as expected under all possible conditions. This type of analysis is commonly used for safety-critical systems, such as those in aerospace, medical devices, or automotive industries, where failures could result in severe consequences.
Style and Cosmetic Analysis
Style and cosmetic analysis enable software teams to enforce coding standards. It checks for stylistic aspects such as consistent formatting, proper indentation, good naming conventions, and other best practices that make the codebase more readable and easier to maintain.
While this type of analysis doesn’t directly impact functionality, it promotes consistency across the project, making it easier for team members to collaborate and understand each other’s code.
Design Properties Analysis
Software teams evaluate the architectural quality of the codebase through an analysis of design properties, which examines complexity, dependencies, and overall maintainability. It highlights areas where the code may be overly complicated, such as functions with too many lines or modules with excessive interdependencies.
Error Checking
Error checking identifies common programming mistakes, such as syntax errors, undefined behaviors, and violations of best practices. It ensures that the code adheres to basic standards for security, reliability, and performance.
This type of analysis acts as a first line of defense against simple but potentially damaging bugs, ensuring that the program is syntactically correct and free of fundamental issues before it’s deployed.
Predictive Analysis
Predictive analysis leverages static code patterns to estimate how the code will behave at runtime. It can detect potential performance bottlenecks, scalability issues, and concurrency problems that might arise as the code executes.
By anticipating these issues early in development, predictive analysis helps teams optimize their code for better performance and stability under real-world conditions, preventing future problems as the software scales.
Best Practices for Effective Static Code Analysis
For best results, static code analysis should be used in conjunction with other testing techniques, such as:
- Dynamic testing after the code has been integrated to test code behavior during execution. Unit, functional, integration, performance, and penetration testing are all dynamic tests that can identify potential static code analysis missed.
- Manual code review in which software developers read through their source code and try to spot defects manually.
- Human testing techniques like usability and user acceptance testing that allow users to identify and report performance issues that your team might not have considered or experienced while creating certain features and functionalities.
To get the most out of static analysis processes and tools, establish internal code quality standards and document coding standards for your project. Customize analysis coding rules to match project-specific requirements.
Integrate static analysis into your development workflow. Pick tools that work with your preferred IDE and continuous integration and deployment (CI/CD) pipeline.
Remember to regularly and routinely update and maintain static analysis tools and rule sets to improve the efficiency of your tools and the breadth of issue types they can identify.
Choosing the Right Static Code Analysis Tool
To get the most out of a static code analyzer, be sure to choose one that supports the programming language your team uses and the coding standards most relevant to your industry.
Codacy is a cutting-edge static analysis tool that supports most major coding languages and standards. It offers customizable code analysis, intelligent project quality evaluation, extensive feedback on your code, and easy integration into your existing workflow.
Give Codacy a spin today by signing up for a free trial.
Static Code Analysis FAQs
1. How can development teams integrate static code analysis without slowing down their workflow?
Brian Pontarelli, CEO of FusionAuth, recommends integrating static code analysis directly into your CI/CD pipeline so it automatically runs with each pull request. This keeps your workflow efficient, catching vulnerabilities early without manual effort.
2. What common challenges do teams face when adopting static code analysis tools?
As Thomas Franklin, CEO of Swapped, noted, "Too much noise kills adoption. A tool that throws hundreds of alerts per scan ends up ignored." Overwhelming noise from irrelevant warnings (false positives) and disruptions caused by the initial setup of tools can slow adoption.
3. How can teams overcome these adoption challenges of static code analysis?
Teams can overcome the challenge of adoption by fine-tuning their static analysis tools to surface only critical issues. Adding exceptions for known false positives and clearly defining pass/fail rules helps maintain productivity and adoption.
Thomas Franklin recommends: "Tuning rule sets to fit project needs prevents unnecessary disruptions. If a specific pattern consistently triggers false positives, adding exceptions keeps scans relevant."
4. How does static code analysis help maintain code quality and scalability over time?
Static analysis catches issues early, reducing technical debt and enforcing coding standards.
Brian Pontarelli, CEO of FusionAuth, has seen tangible improvements in code quality and early bug detection. "By catching these issues early on, the foundation remains strong which allows solutions to grow and evolve with minimal rework."
5. What's the advantage of integrating static analysis into regular code reviews?
Throwing static analysis into code reviews is a good way to make sure that potential vulnerabilities are caught before merging code, without disrupting productivity.
Artem Razin, CEO of Softanics, described the benefit of this process for their company: "This integration felt natural and enhanced regular code reviews without disrupting productivity."
.svg)