Further Enterprise security analysis for Scala

We’re excited to announce the latest addition to our suite of security analysis: Spotbugs.
SpotBugs is a program which uses static analysis to look for bugs in Java code. It checks for more than 400 bug patterns. SpotBugs is the successor of FindBugs, an open-source static code analyzer.
SpotBugs picks up from the point FindBugs leaves off. At the same time, it maintains the support of the Findbugs’ community.
We’ve also bundled Find Security Bugs: a SpotBugs plugin for security audits of Scala web applications. The issues reported cover the OWASP Top 10 and CWE standards.
It includes security patterns such as Potential Path Traversal, Potential Command Injection, Potential SQL Injection, Potential XSS and others.
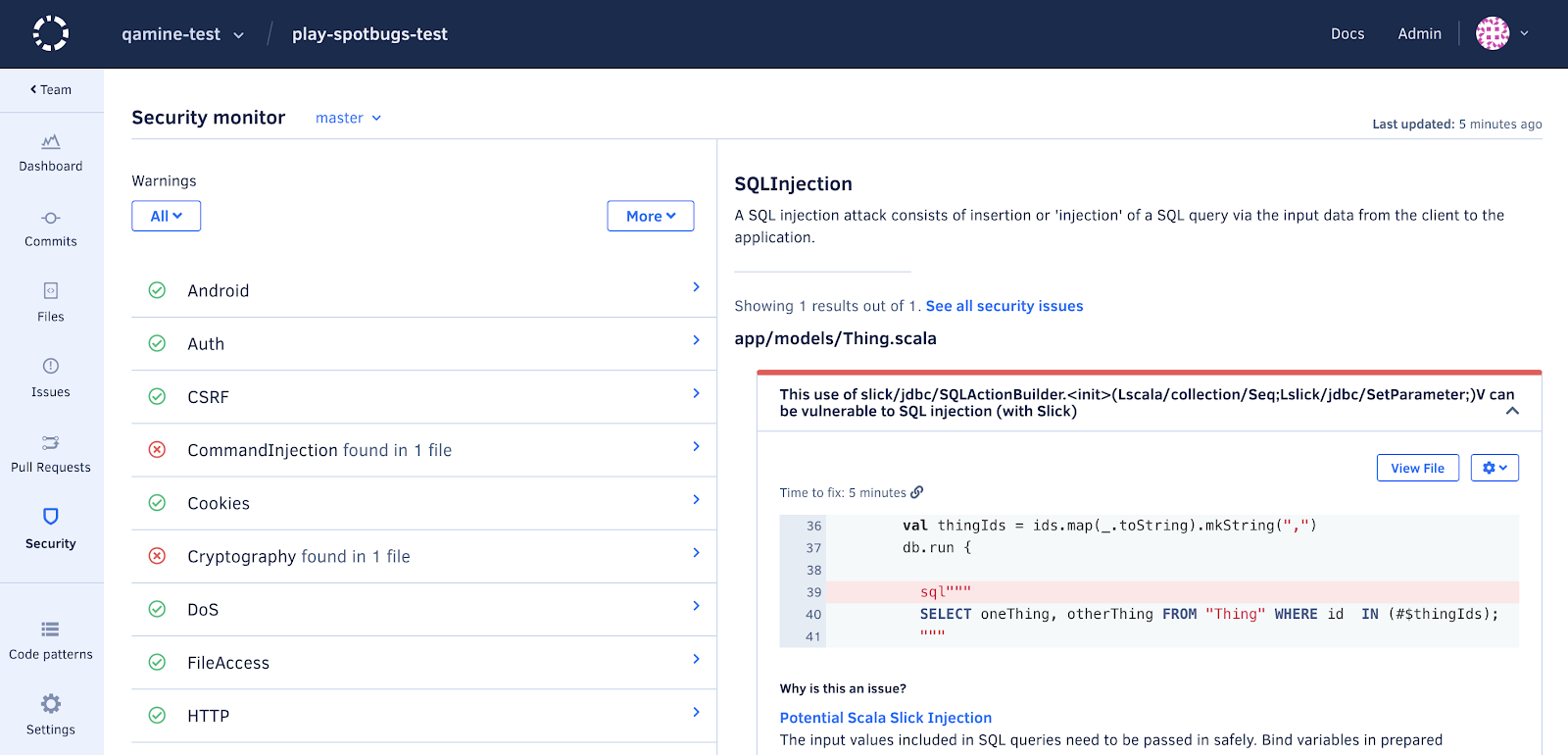
Failure to use bound variables in prepared statements leaves you at the risk of attackers performing SQL injection.
Try it out for yourself:
- git clone https://github.com/qamine-test/play-spotbugs-test.git
- sbt compile
- codacy-analysis-cli analyse –tool spotbugs –directory `pwd` –allow-network
We’re making these new patterns available for Self-hosted users in the next update for Apex, PHP, C/C++, Shell script, Dockerfile, Visual Basic, Elixir, PowerShell, TSQL and Groovy, besides the existing C#, Java, JavaScript, Python and Ruby support. You can get started by following our guide to run Spotbugs.
If you haven’t tried Codacy yet, contact us to install Codacy on-premise.
.svg)


