Codacy Platform
.png?width=1740&name=Feature_MaliciousPackage-Blog%20(1).png)
11/12/2025
In recent weeks, we’ve witnessed a wave of sophisticated supply chain attacks where npm packages were compromised, most notably the Shai-Hulud 2.0...

04/12/2025
The widespread adoption of AI coding tools is starting to feel like a 'Wild West' for devs, engineering leaders and compliance officers alike. With ...

30/10/2025
Developers have fully embraced AI coding tools, and they are not planning to let go. They ship more, debug faster, and automate the tedious parts of...
23/10/2025
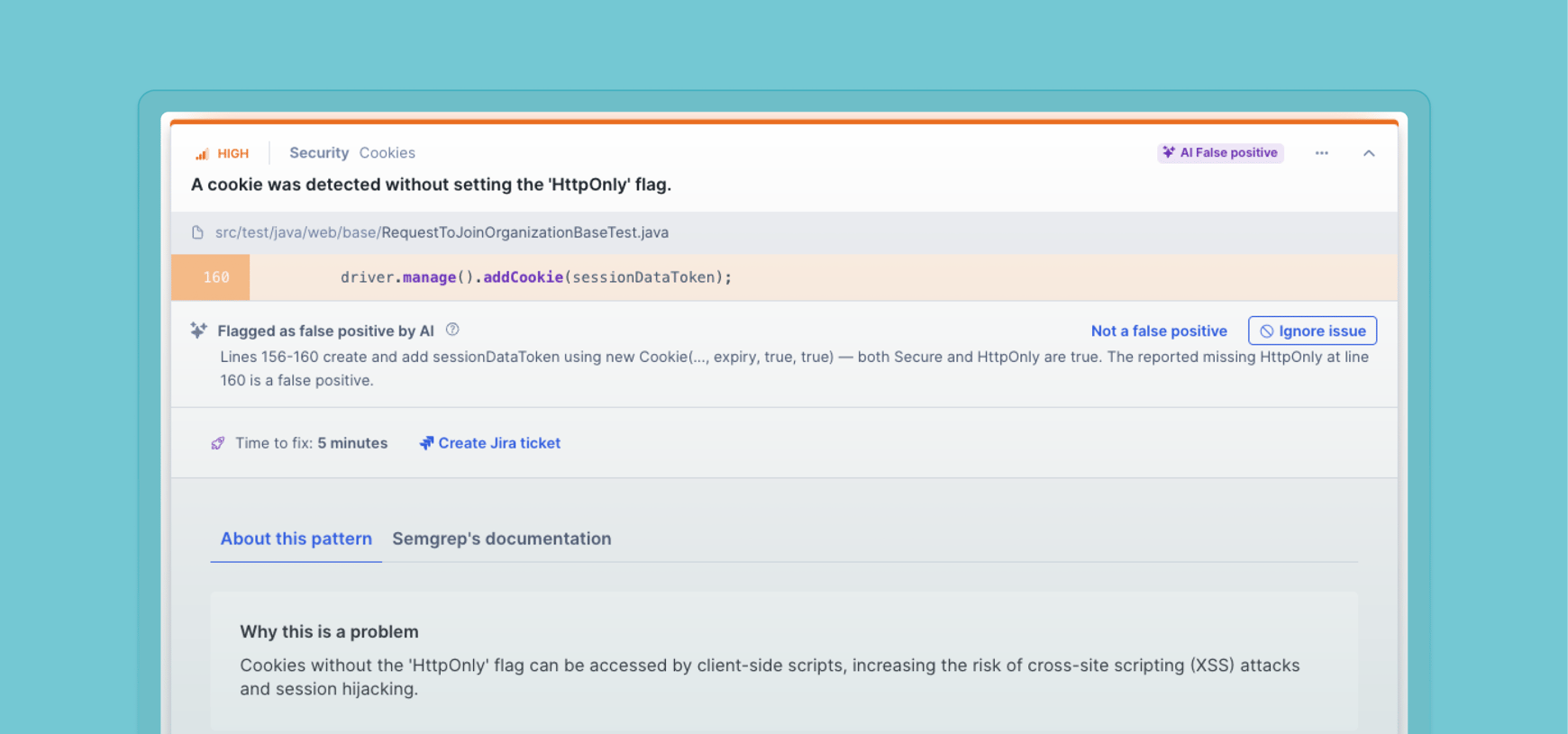
Every developer has been there: You push your code, the scanner runs, and your PR checks light up with new alerts. You instinctively know you are not...
10/10/2025
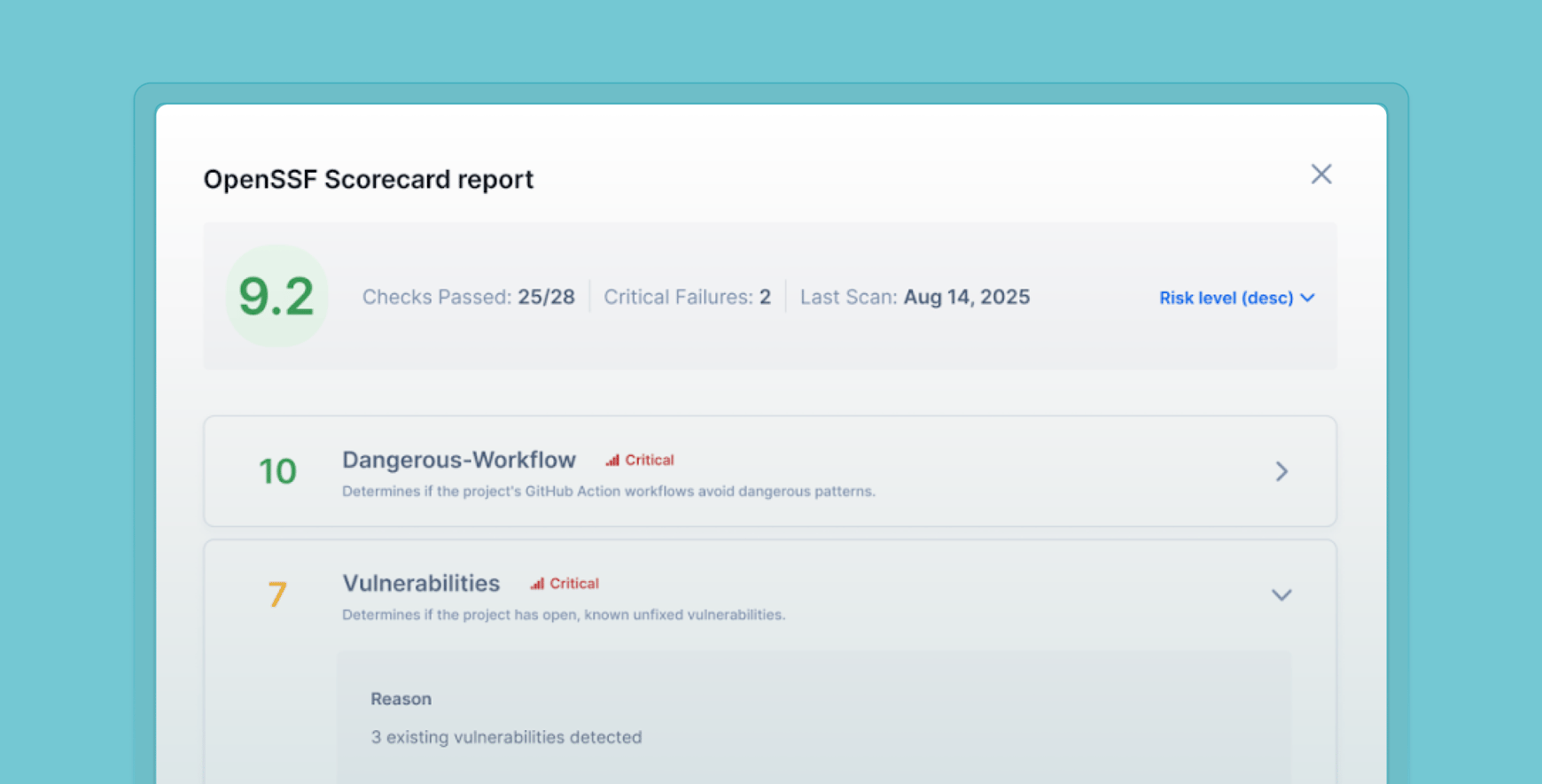
In modern software development, we run on open-source. It’s the engine of innovation, allowing teams to build faster, smarter, and more efficiently....

18/09/2025
We migrated our SPA from Create React App to Vite and Jest to Vitest to escape security vulnerabilities, dependency constraints, and slow builds
Subscribe
to our blog
Stay updated with our monthly newsletter.
.svg)
