- April 11 2024
- Codacy

- April 9 2024
- Jaime Jorge
Into the Breach: Business Survival in the Age of Accelerating Cyber Threats
READ MORE
- March 17 2024
- Codacy
Displaying Pen Testing Results in the Security and Risk Management Dashboard
READ MORECodacy Security (9)

11/04/2024
The speed at which software development companies deliver their products has become a paramount differentiator. Amidst the rush to deploy cutting-edge...

09/04/2024
We spend around $215 billion per year on cybersecurity between vendors, practices, and tools, and this has been increasing.

28/03/2024
According to research by Statista, over 353 million individuals were impacted by data breaches and leaks in 2023 alone. Many of these breaches stem...

19/03/2024
Threats are pervasive in modern software development. These threats don’t just come from 1337 h4x0rz; they come from you. The sophistication of modern...
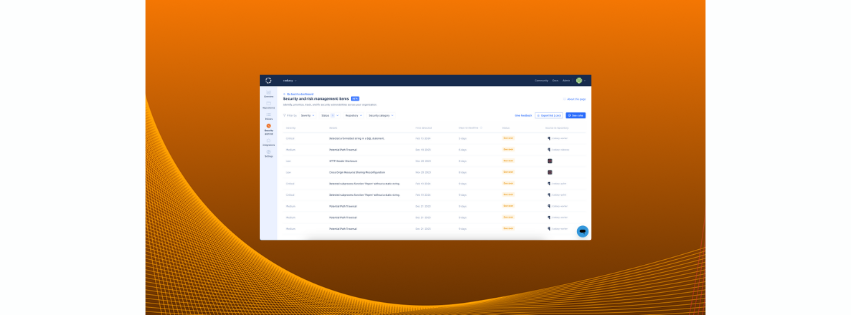
17/03/2024
As part of our January 2024 Product Showcase, we announced the availability of penetration testing services via Codacy Security for customers with...
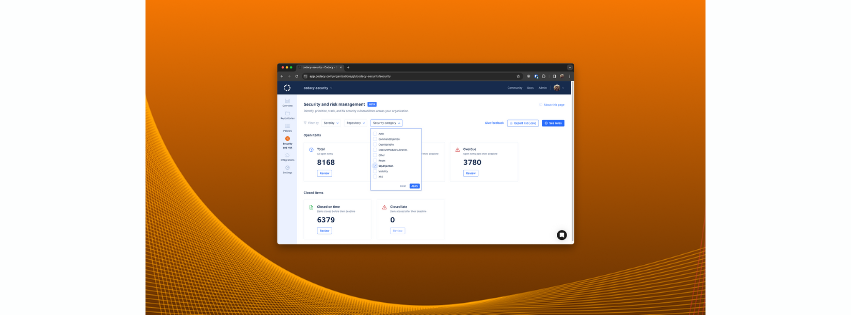
13/03/2024
While constantly adding new ways to check your code for security issues is incredibly important to us, being able to present that data to you...
Subscribe
to our blog
Stay updated with our monthly newsletter.
Platform
By Audience
2025 CODACY
.svg)