- October 10 2024
- Codacy

- September 1 2024
- Codacy
Codacy Security Adds Thousands of New SAST Rules With Semgrep Integration
READ MORECodacy Security (3)

10/10/2024
In 2022, there were 1,802 data compromises in the U.S. alone. In 2023, that number soared to 3,205, and it will only continue to increase as bad actors...

28/09/2024
In 2017, attackers wreaked havoc for 76 days before Equifax finally discovered the breach. Several security lapses had allowed attackers to access the...

24/09/2024
Many software developers use AI coding assistants like ChatGPT and GitHub Copilot to significantly speed up their development process, relying on them...

21/09/2024
Imagine moving to a new house, packing each box with specific items, and labeling them clearly. You want to ensure each box is secure, that nothing...
11/09/2024
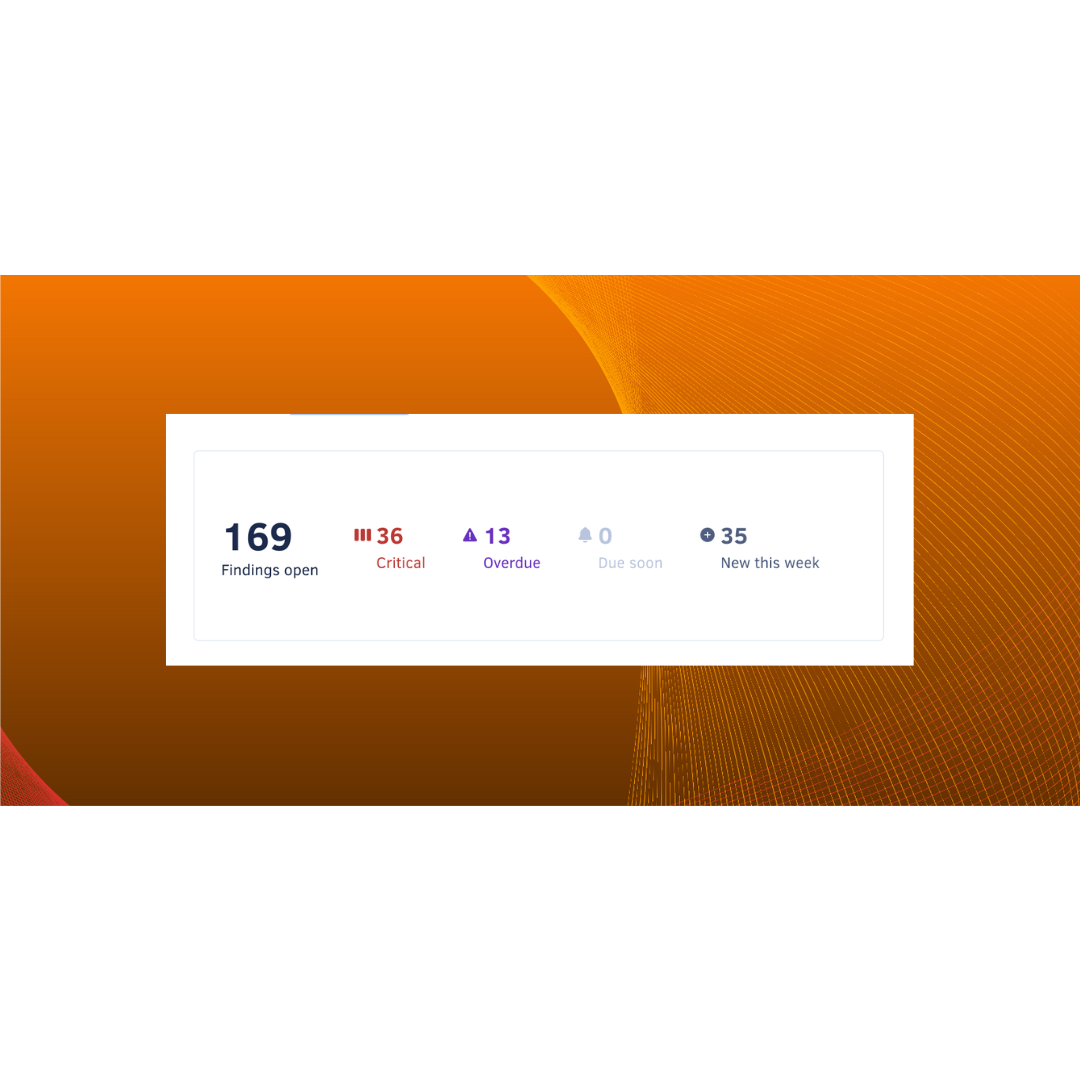
We’re excited to announce the launch of our proactive software composition analysis (SCA) scans, which are available to all our business-tier...
01/09/2024
If 2023 taught us anything, it’s that code quality and code security are inextricably linked. Their main commonality? They are both required upstream...
Subscribe
to our blog
Stay updated with our monthly newsletter.
Platform
By Audience
2025 CODACY
.svg)



