- July 24 2024
- Codacy

- July 24 2024
- Codacy
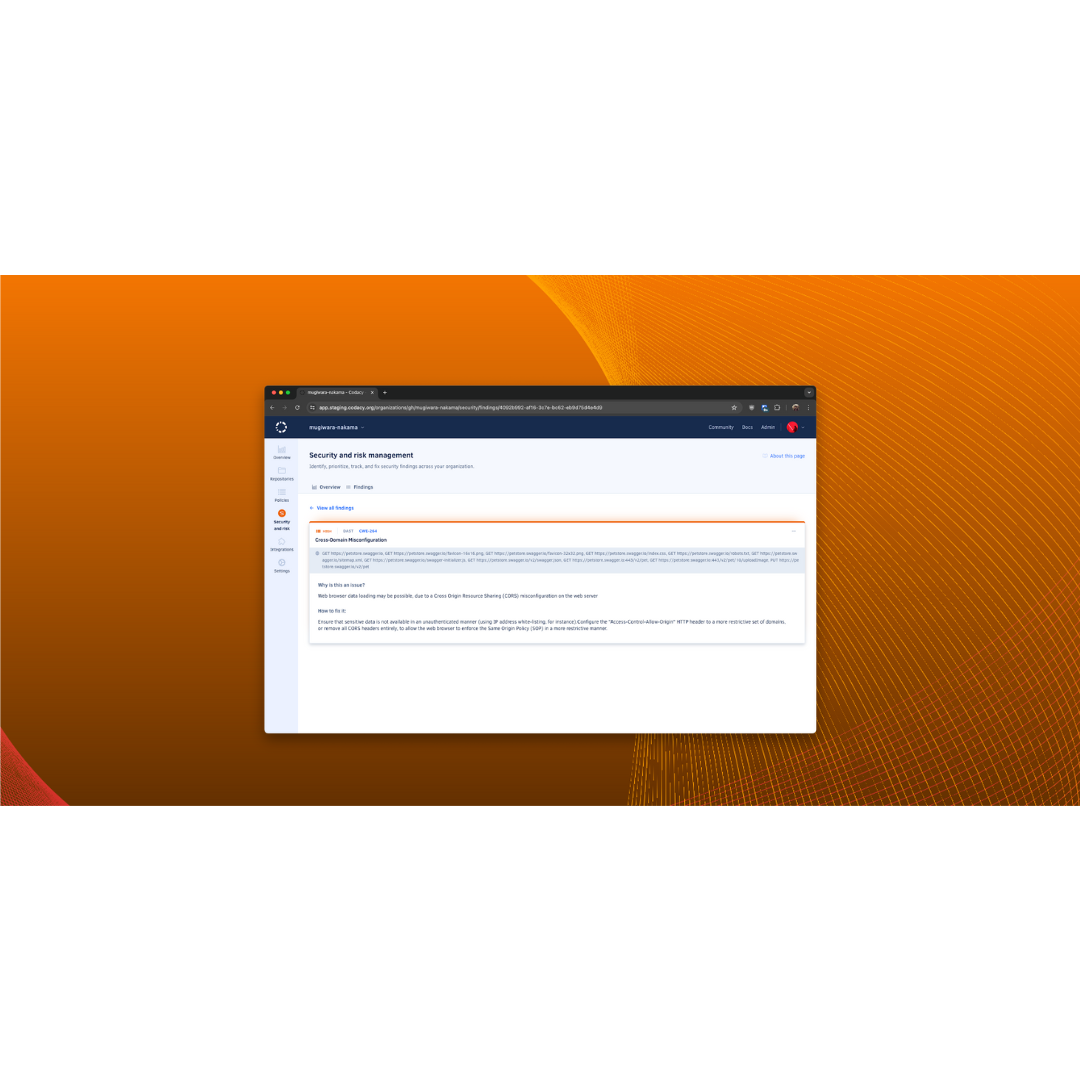
Codacy Security Now Includes Dynamic Application Security Testing (DAST)
READ MORECodacy Security (5)

24/07/2024
Companies are increasingly prioritizing security to combat the growing threat of cyber attacks. Our 2024 State of Software Quality report shows that...
24/07/2024
We're thrilled to announce that Codacy Security now includes Dynamic Application Security Testing (DAST) capabilities!

23/07/2024
Open-source software has become an integral part of modern software development. For example, over 93% of developers use Git, the open-source version...

16/07/2024
Imagine you're building a house. In the design phase, you decide on the layout, structure, and materials. You choose the number of rooms, where the...

09/07/2024
Every developer will always have that gnawing doubt in the pit of their stomach once they hit “Commit changes.”

05/07/2024
Java is a cornerstone of modern software development, powering everything from enterprise-level applications to Android apps and large-scale data...
Subscribe
to our blog
Stay updated with our monthly newsletter.
Platform
By Audience
2025 CODACY
.svg)



