- December 11 2024
- Codacy

- November 6 2024
- Codacy
New Feature: Assigning Multiple Coding Standards to a Single Repository
READ MORECodacy Security (2)

11/12/2024
Continuous Integration/Continuous Development (CI/CD) pipelines lie at the core of the DevSecOps philosophy. CI/CD streamlines software delivery by...

10/12/2024
Building software with open-source components isn’t always the best idea. Licenses dictate how you can use, change, or share these components. And if...

27/11/2024
Clean code is similar to a well-written article. Good articles possess certain characteristics that make them a pleasure to read: clear and accessible...
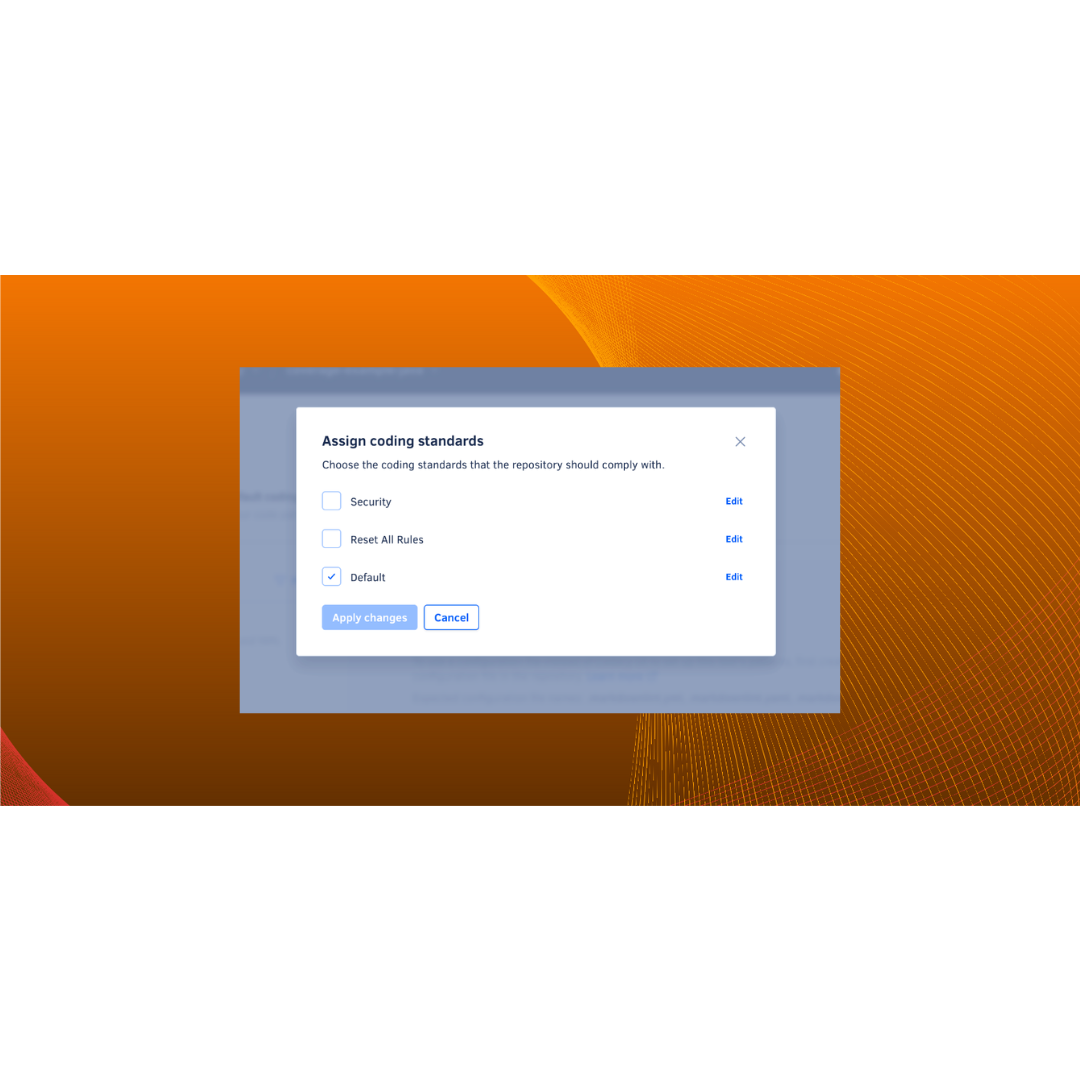
06/11/2024
We’re excited to share a major update: you can now assign multiple coding standards to a single repository.

30/10/2024
Investors love big ideas. But they need proof that the technology underneath can actually handle the job. A flashy pitch means nothing if the systems...

12/10/2024
Security vulnerabilities are a constant threat to organizations of all sizes. Often discovered through Common Vulnerabilities and Exposures (CVEs),...
Subscribe
to our blog
Stay updated with our monthly newsletter.
Platform
By Audience
2025 CODACY
.svg)





